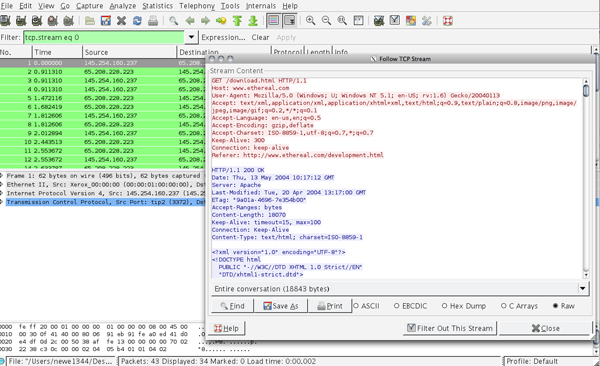
I was talking with a friend about “listening” in on other peoples wireless connections. He didn’t realize how easy it is for someone to audit an open network and begin tracking online activity. Like most things mischievous online, the barrier to entry is an indicator of how likely an attack is. Take WEP cracking for example, all you need is a packet capture program and rainbow tables and you’re in. Most of the hard work is done for you. However, listening in on networked conversations is even easier, which means, potentially more people are doing it.
Here’s how:
- Download Wireshark.
- Install and start a packet capture.
- Right click and follow a TCP stream.
That’s it. You’ll literally be able to read anything over your network in plain text as long as the connection is not through https and the wireless network is not encrypted.
It gets more complicated if you want it to be. I’m sure everyone is well aware, but I’ll reiterate, one should never use Wireshark to audit a network that one doesn’t have permission to audit. However, bad apples do exist, so if you have an unsecured wireless network, consider it public and never login to important sites while on it.